PERSONAL PRIVACY AND ENCRYPTION
IN DECODE 'S RESEARCH
Visit
Collaboratlons ostablished
Hospitals
Cifnies
Physlclans
•
Research project approvals
•The Data Proteetlon Commission
•The National Bloethlcs Commlttee
•
Creation of patientlist
Name· social security number
(1212555969)
Encryptlon key
kept by the Data
Proteetlon
Name -SS
-1
PN
Data protection
the data of all personal
Identifiera and encrypt
the soclal seeurity
number uslng 128-btt
symmetrtc
encryptlon algortthm.
Encrypted social securlty number
XGFTREN
~ ~~
PN · SN
+
Sam
p
les
seanned
PN · phenotype
and relabeled
~rver
iSN
El
~:
~internal
EJ
~
~sampleno.
~
=~: :~~: ~~~
ONA
;
PN· phenotype
PN
list
.1"
Encrypted
PN
-genotype
Laboratory
genealogy database
t>
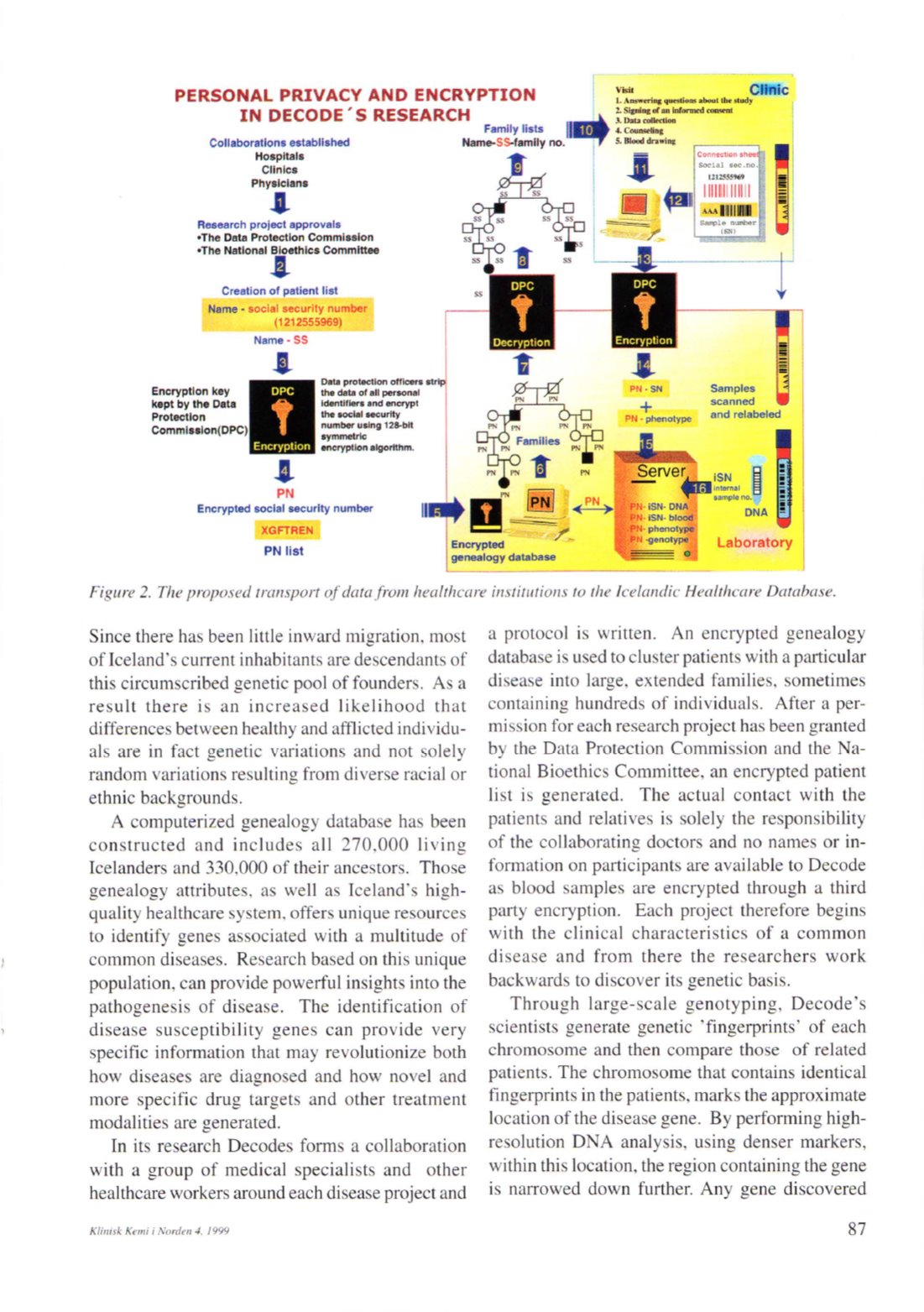
Figure
2.
The proposed transport ofdatafrom hudtheare institutions to the leelandie Healthcare Database.
Since there has been little inward migration, most
oflceland's current inhabitants are descendants of
this circumscribed genetic pool of founders. As a
result there is an increased Iikelihood that
differences between healthyand afflicted individu–
als are in fact genetic variations and not solely
random variations resulting from diverse racial or
ethnic backgrounds.
A computerized genealogy database has been
constructed and includes all 270,000 li ving
leelanders and 330,000 of their ancestors. Those
genealogy attributes, as well as Iceland's high–
quality healthcare system, offers unique resources
to identify genes associated with a multitude of
common diseases. Research based on this unique
population, can provide powerful insights into the
pathogenesis of disease. The identification of
disease susceptibility genes can provide very
specific information that may revolutionize both
how diseases are diagnosed and how novel and
more specific drug targets and other treatment
modalities are generated.
In its research Decodes forms a collaboration
with a group of medical specialists and other
healthcareworkers aroundeachdiseaseproject and
Klinisk Kemi
i
Norden 4. /999
a protocol is written. An encrypted genealogy
database is used to cluster patientswith a particular
disease into !arge, extended families, sometimes
containing hundreds of individuals. After a per–
mission for each research project has been granted
by the Data Protection Commission and the Na–
tional Bioethics Committee, an encrypted patient
list is generated. The actual contact with the
patients and relatives is solely the responsibility
of the collaborating doctors and no names or in–
formation on participants are available to Decode
as blood samples are encrypted through a third
party encryption. Each project therefore begins
with the clinical characteristics of a common
disease and from there the researchers work
backwards to discover its genetic basis.
Through large-scale genotyping, Decode's
scientists generate genetic 'fingerprints' of each
chromosome and then compare those of related
patients. The chromosome that contains identical
fingerprints in the patients, marks the approximate
location of the disease gene. By performing high–
resolution DNA analysis, using denser markers,
within this Iocation, the region containing the gene
is narrowed down fmther. Any gene discovered
87


